Bloodhound is very useful for red teaming in the Active Directory environment and can easily identify attack paths which can be used for both lateral movement and privilege escalation. But from the blue team or system administrator point of view in large corporates, it can be difficult to use BloodHound easily.
The important problem with attack paths is the identification of the most dangerous attack paths from millions. Sometimes one relationship that we block (Group Membership, ACE, Session, etc.) can block access to Tier0 objects with eliminating thousands of attack paths.
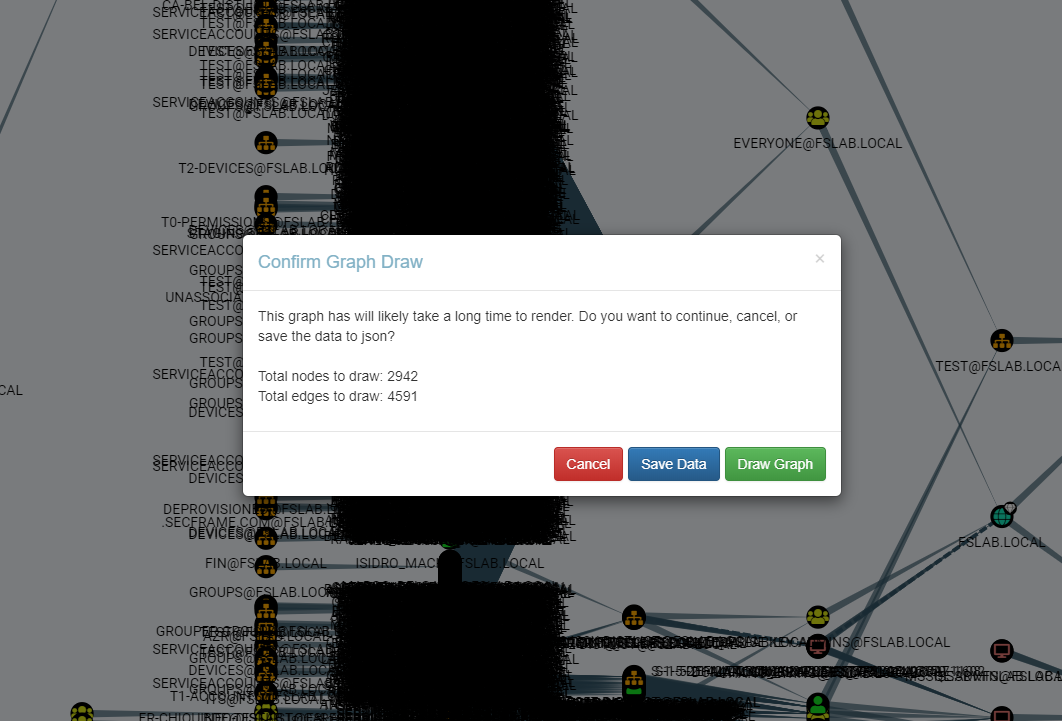
In this blog post, we will discuss how to prioritize and mitigate attack paths in an Active Directory environment using Bloodhound and our new tool Kangal.
By applying the processes iteratively and systematically in your own environment, you can have a fairly secure Active Directory environment, both in terms of attack paths and privileged access. In this way, the maneuvers of attackers, especially in Ransomware cases, will be restricted as much as possible.
You can download Kangal from here
Kangal and Combined Attack Path Management
The Combined Attack Path method is a process to summarize and combine attack paths that target Tier0 objects in an Active Directory environment. In this way, it is possible to focus on the relationships that are the riskiest among the millions of attack paths and that can have the most impact when mitigated.
Kangal analyzes the data collected with Bloodhound to create a Combined Attack Paths graph and scores the groups created. According to these scores, dangerous relationships can be easily prioritized.
After we collect the data with Sharphound and upload this data to the Neo4j database via BloodHound, we can start our analysis.
When we run the Find Shortest Path to Domain Admins query with BloodHound, we get the following output. Although this output can be useful for the red team, it is not much suitable for blue team processes.
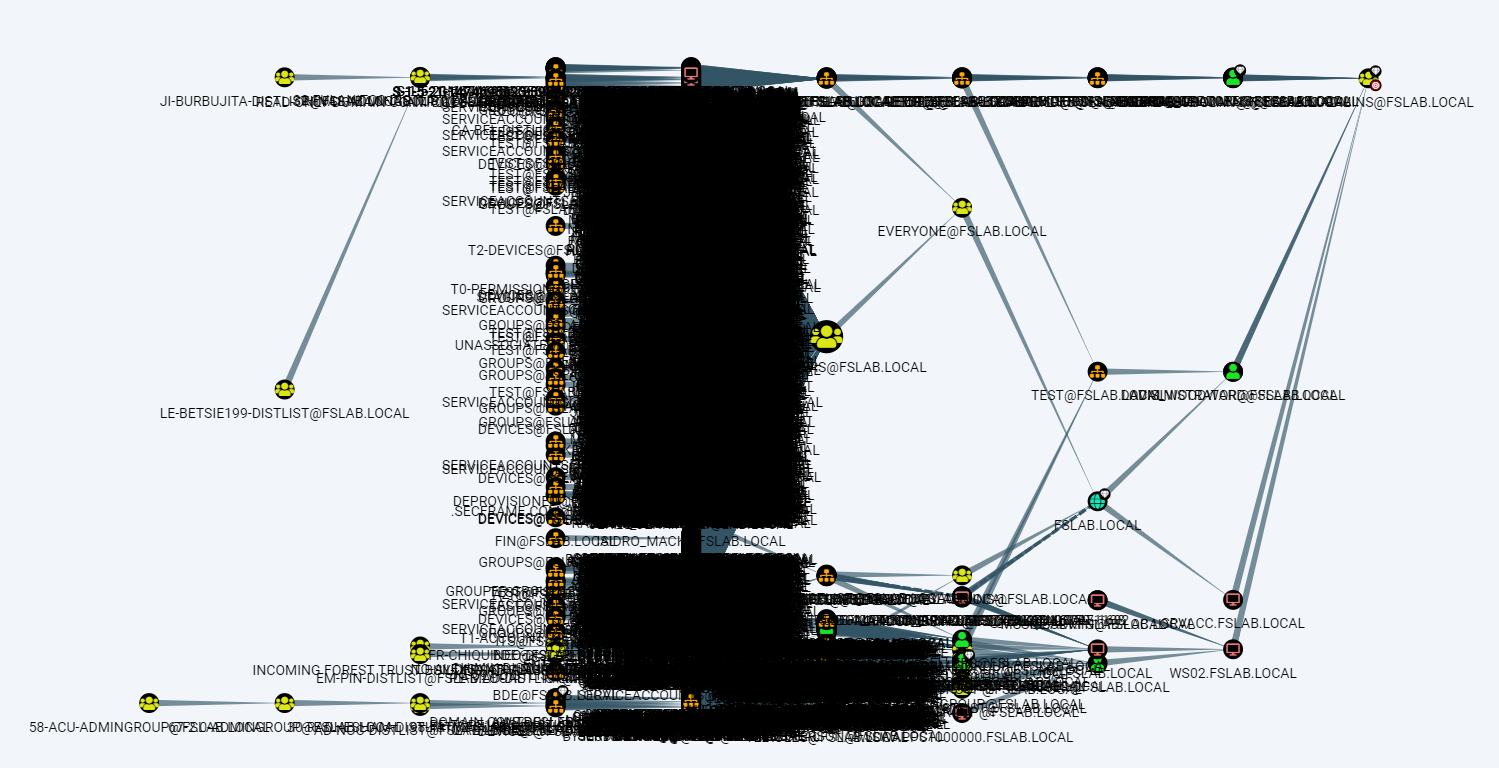
BloodHound Find Shortest Path to Domain Admins Query Result
The Shortest Paths to High Value Targets query gives a similar output, and it can be difficult to examine this output through the BloodHound interface in a large environment.
BloodHound Shortest Path to High Value Targets Query Result
Finally, the statistics produced by BloodHound for the test environment are as follows.
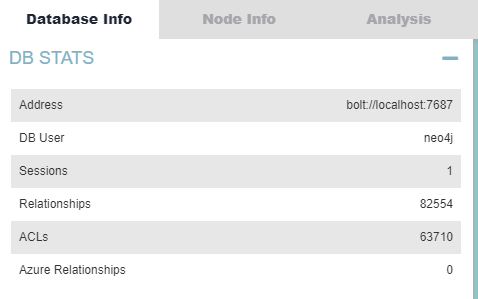
BloodHound Database Stats
Analysis Process
1. Identifying the Tier0 Objects
As a result of the Bloodhound enumeration, various objects (Domain Admins, Administrators, etc.) are marked as high value. But BloodHound does not mark
- members of these admin groups,
- OUs containing these admin objects,
- GPOs that affect them
- and some other privileged groups as high value.
- High value objects should be listed and examined with the following Neo4j query. If there are different important /privileged objects in the corporate other than these objects, they should also be marked as high value. This operation can be performed from the BloodHound interface or via Neo4j.
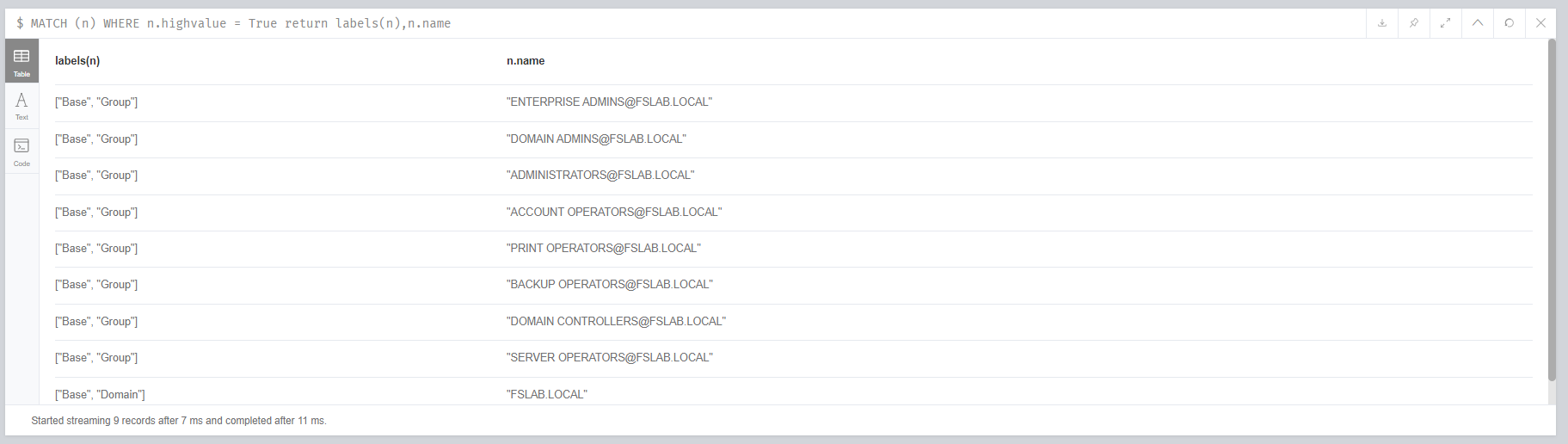
Identifying high values objects and their labels (9 objects)
- After the review and marking, all members of the high value groups should also be marked as high value with the following Neo4j query.
- With the following Neo4j query, Container and OU objects that contains high value objects should be marked as high value in the same way.
- With the following Neo4j query, Group Policy Objects linked to high value domain or OU objects should also be marked as high value.
- Finally, with the Neo4j query below, objects marked as high value (i.e. Tier0) should be listed and reviewed again. If there are objects that should not be high value, the permissions of these objects should be revoked and the SharpHound enumeration should be repeated. After that, all steps above should be repeated.
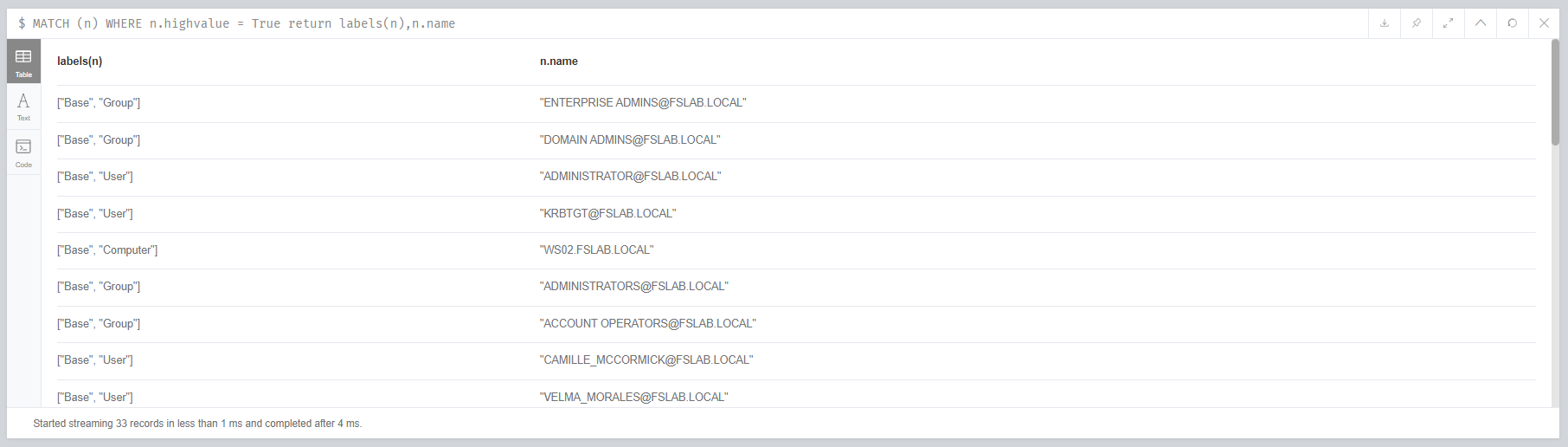
Identifying high values objects and their labels after the queries(33 objects)
2. Creating a Combined Attack Path Tree
After marking the Tier0 objects, the Combined Attack Path tree can be created on Neo4j by running the Kangal. After installing the required packages, Kangal should be run with the following command with Neo4j username and password.
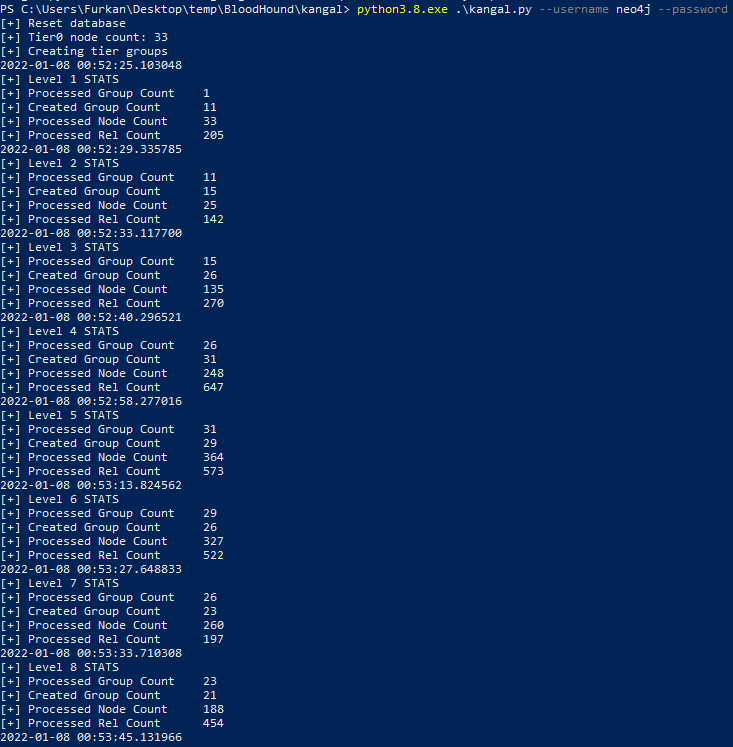
Starting Kangal through Powershell
When the operation is completed, the following Neo4j query can be run with the BloodHound interface and the combined attack paths can be seen.
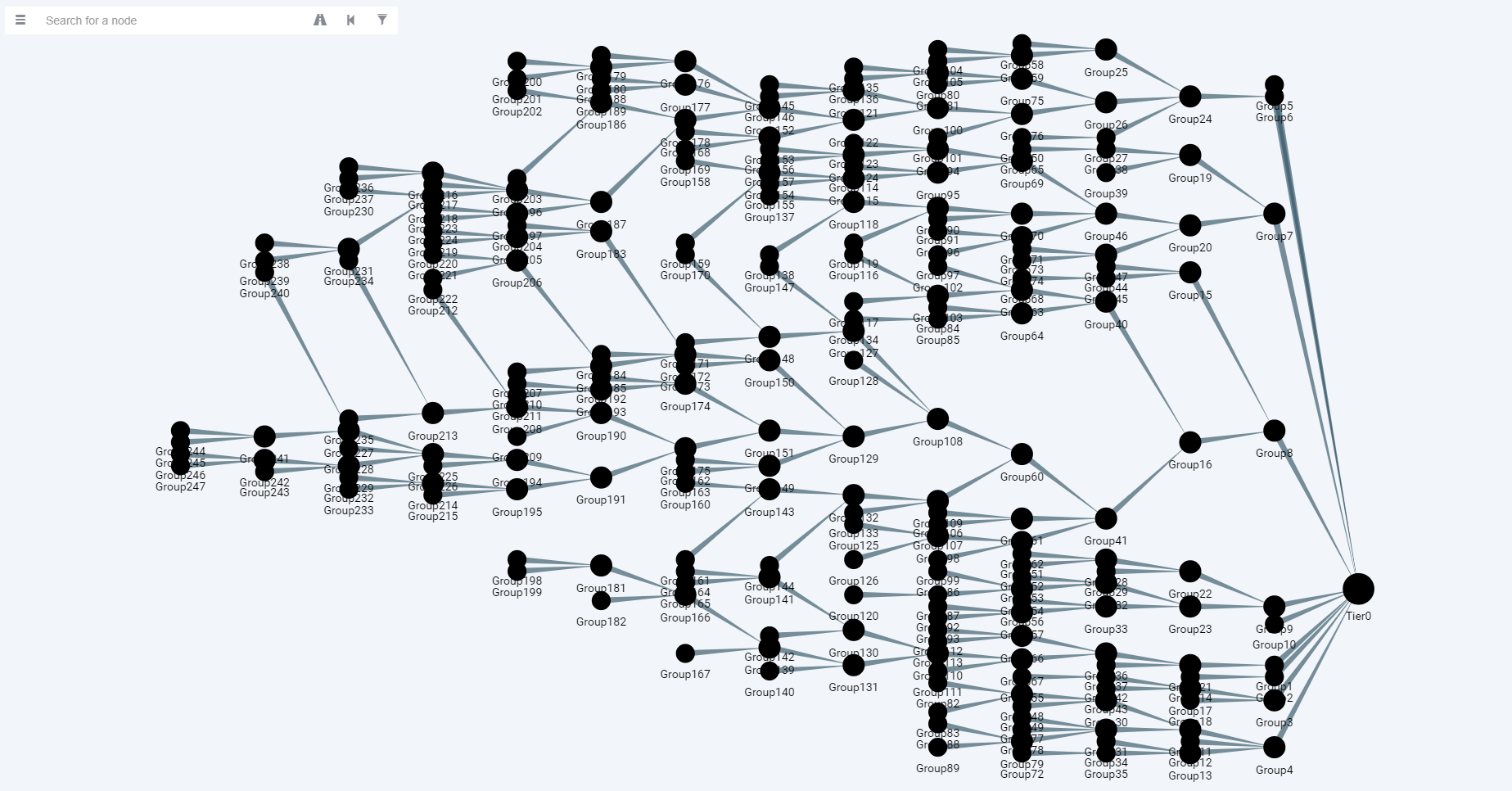
Visualizing Combined Attack Path Tree with BloodHound
Thanks to the attack tree, the data that were difficult to analyze at first was grouped and made more concise. When the attack paths in this tree are examined, it can be easily seen that the paths to Tier0 are collected under some groups. As an example, when we decouple the connection between Tier0 and Group8, we can prevent all groups under Group8 from reaching Tier0 as well. Thus, with few operations, we can eliminate a huge risk.
Before starting to mitigate the attack paths, we can detect the risk scores of Tier objects with the following query.
As a result of this query, we can see the following values on the Table tab in the Neo4j.
| Attribute | Description |
|---|---|
| level | Distance to the Tier0 object |
| sum_child_count | Recursive total child count of Tier object |
| members | objectid values of members which belong Tier object |
| name | Name of the Tier object |
| index | Index of the Tier object |
| sum_member_count | Recursive total child member of Tier object |
Sum_member_count is very important for us within these values. This value indicates how many users in the Active Directory environment can access to the Tier0. For example, for Tier0, this value is 2583. This means that 2583 unprivileged Active Directory objects can compromise Tier0 objects. This value can also be obtained with the following query.
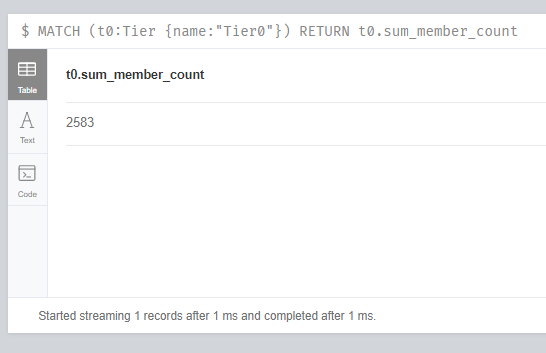
Querying sum_member_count of Tier0
3. Elimination of Attack Paths
After determining the risk score on Tier0 objects, the process of eliminating attack paths should be started by prioritizing them. We can use sum_member_count metric for prioritization. The following Neo4j query lists the 5 most risky groups (which have most members) related to Tier0.
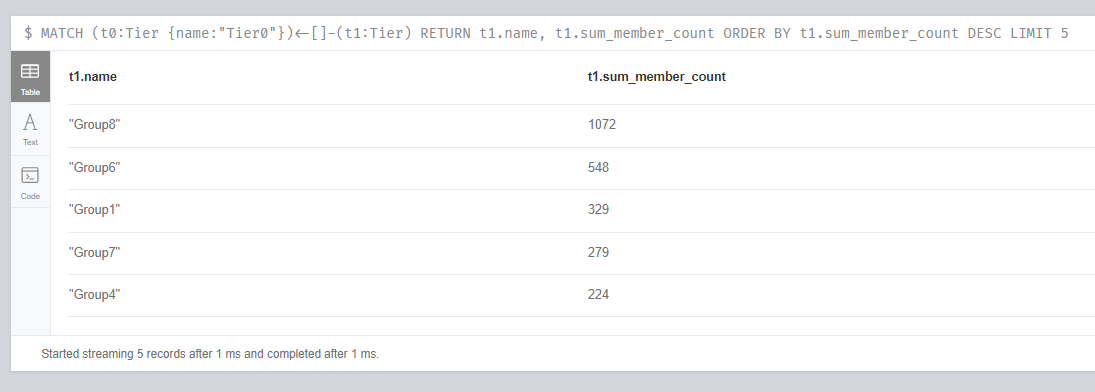
Identifying most risky 5 groups which have relation on Tier0
The following Neo4j query can also be used to determine the members of these groups and what relations these members have over Tier0. We call the objects that are not members of Tier0 but have privileges on Tier0 as Stealth Admins.
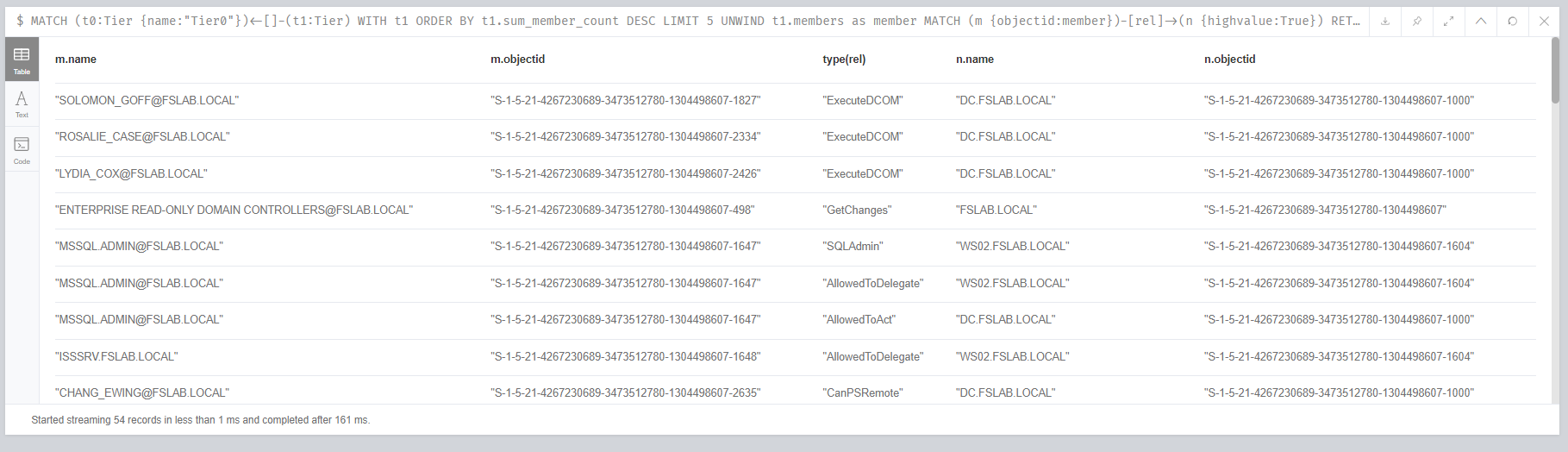
Identifying risky objects and their relations on Tier0 objects
The output also shows that the Enterprise Read-Only Domain Controller group has GetChanges privilege on the domain object. This privilege is normal and default for Active Directory. Therefore, Enterprise Read-Only Domain Controller group should also be marked as highvalue. Objects identified as privileged like this group during the analysis process should be noted and marked as highvalue in the next iteration.
To analyze this output more easily, we can get a unique list of affected objects in the Tier0 group with the query below.
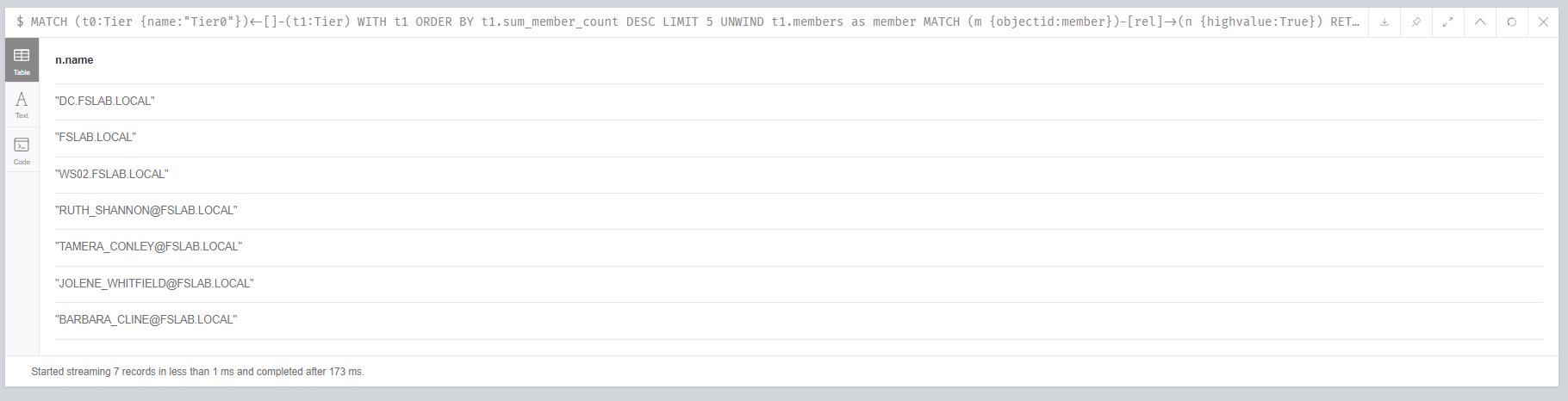
Identifying affected Tier0 objects
After the list is obtained, dangerous or improper privileges over Tier0 objects should be examined and mitigated step by step.
For example, when the Security tab of the fslab.local domain object is opened, the ACL values on this object can be seen. Unnecessary, broad, or suspicious entries should be removed or restricted. For example, in this interface, we can see that the group CO-blackgirl-admingroup has FullControl(GenericAll) privilege over the domain and all objects under the domain. This privilege is a very broad one and that should only exist for certain admin objects. Therefore, these and similar entries should be removed.
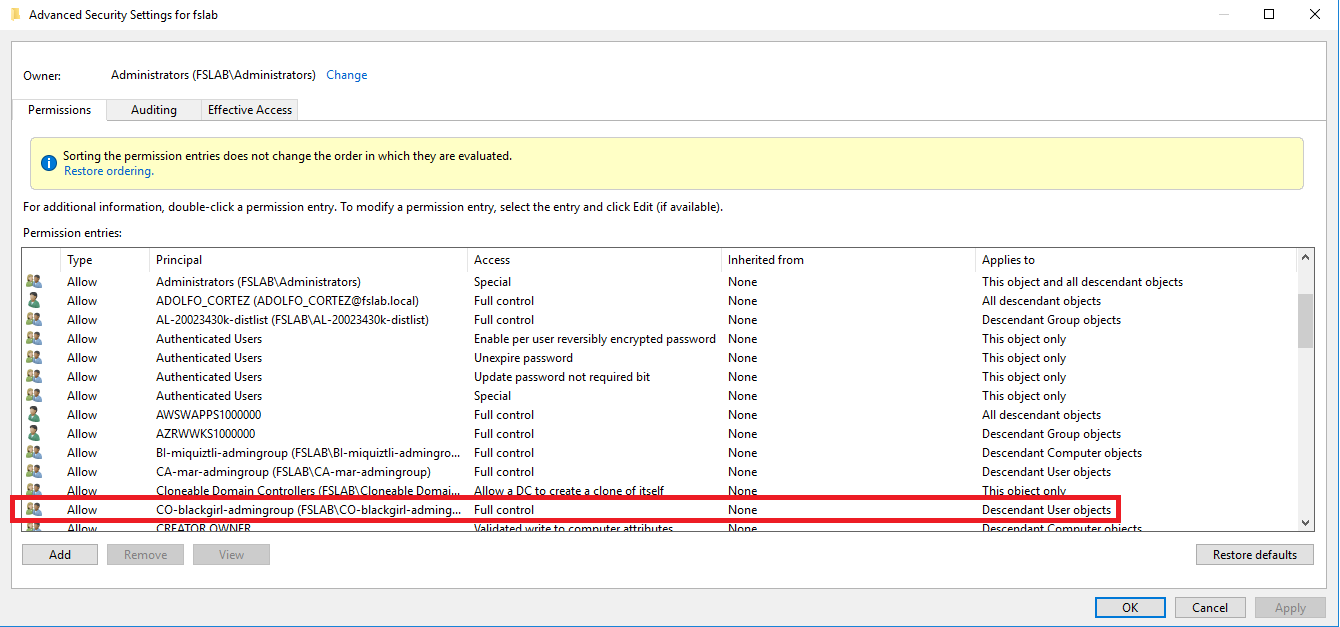
Dangerous access control entries on fslab.local domain object
In other case, three users with ExecuteDCOM privilege over the DC were identified. This privilege is due to the Distributed COM Users group membership. For this reason, users who do not need this privilege should be removed from this group.
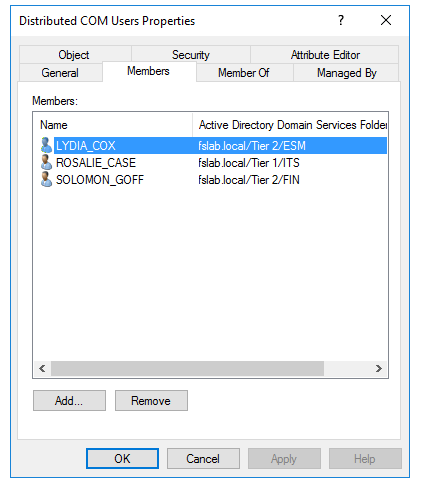
Members of Distributed COM Users group
In our last example, we can see the ACL information on the BARBARA_CLINE object. The key point here is that the JO-teamojavi-admingroup group has FullControl(GenericAll) privilege on the BARBARA_CLINE not directly but because of inheritance. This ACE was actually applied to the FSR OU which the BARBARA_CLINE is a member. But it also affects the BARBARA because of ACL inheritance.
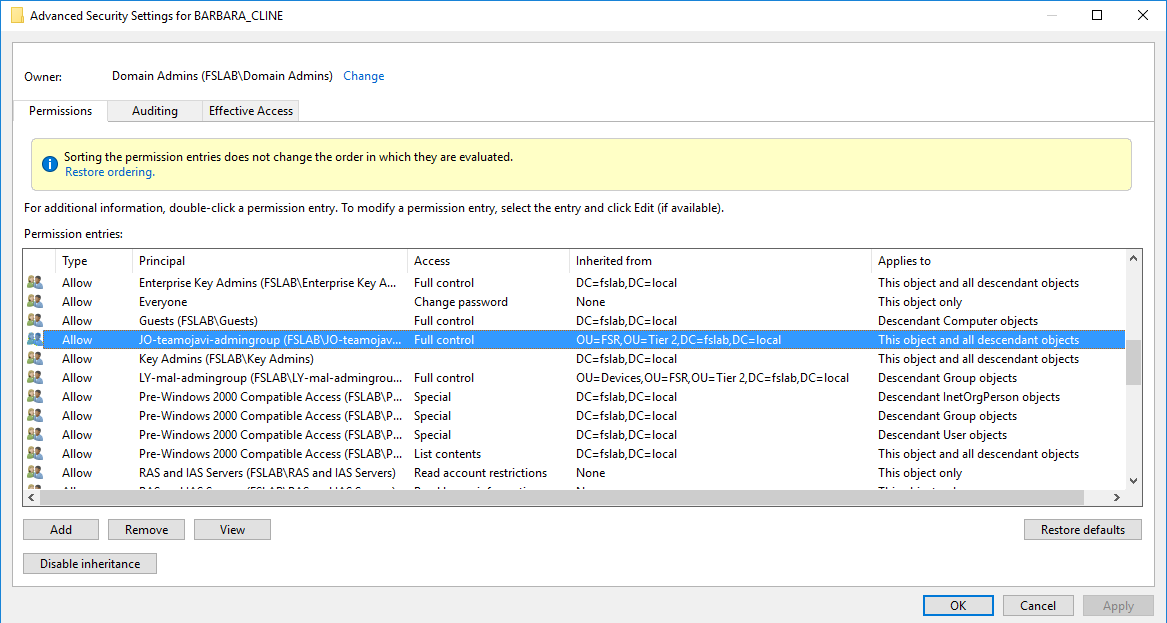
Interited Access Control Entries
Results
After these steps are completed and the dangerous relationships are cleared, the analysis process should be repeated from the first stage. Later, we started new SharpHound enumeration in test environment and obtained statistics below.
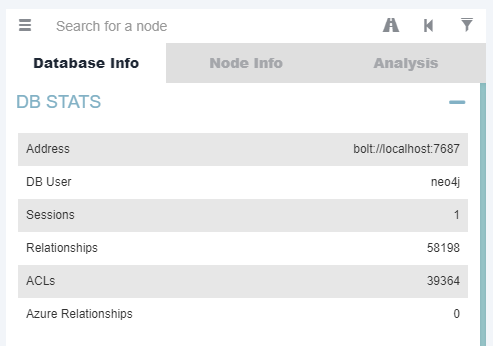
Database stats after analysis process
In addition, after all steps are done and the Combined Attack Path tree is created again, we can get a visual like below. It can be seen that the attack paths are reduced compared to the first tree.
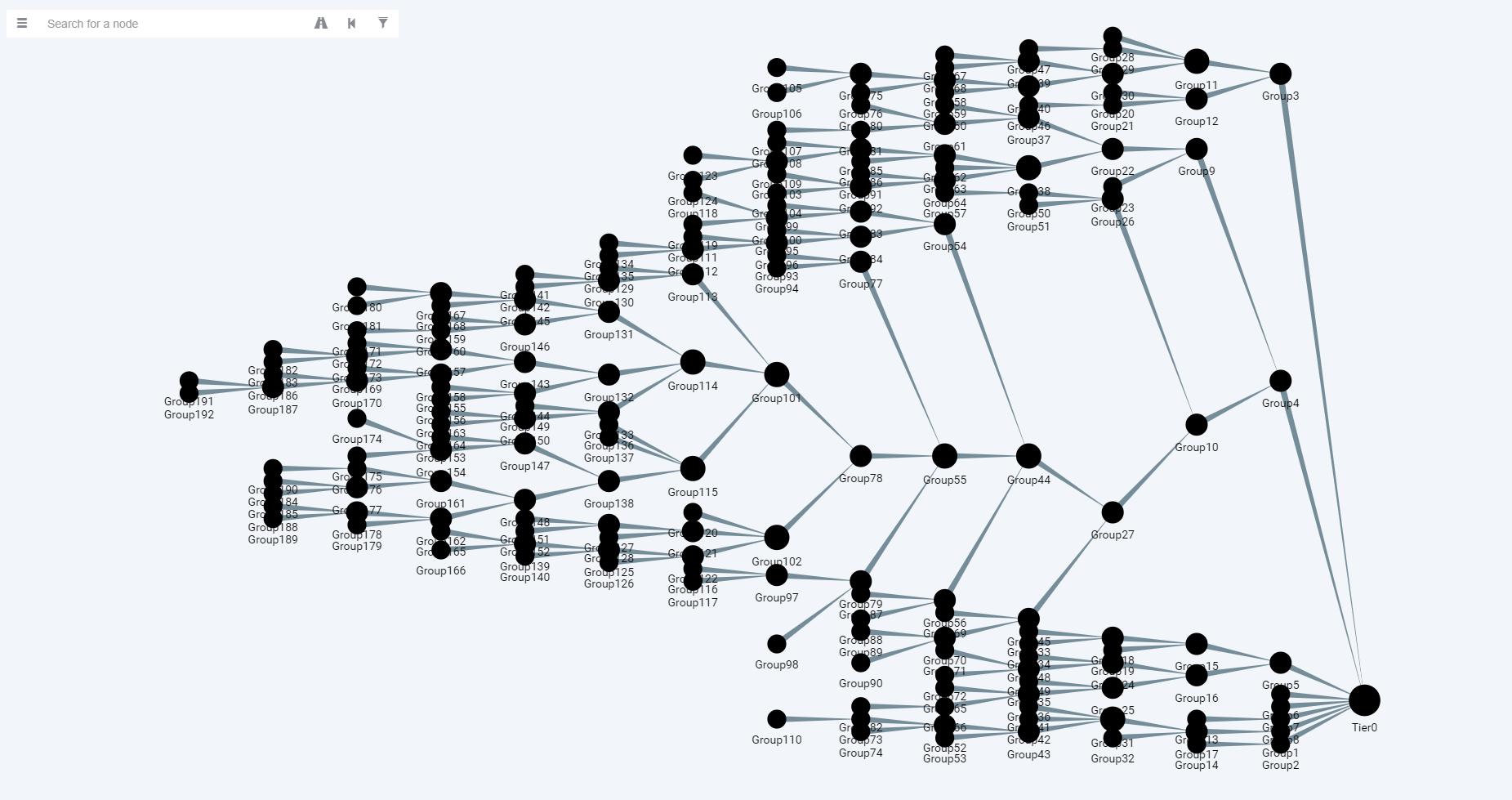
Combined Attack Path Tree after analysis process
Also, in the second iteration, the sum_member_count value on the Tier0 object is reduced by half.
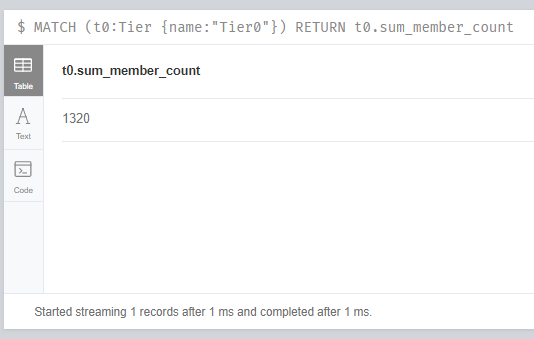
sum_member_count of Tier0 object after analysis
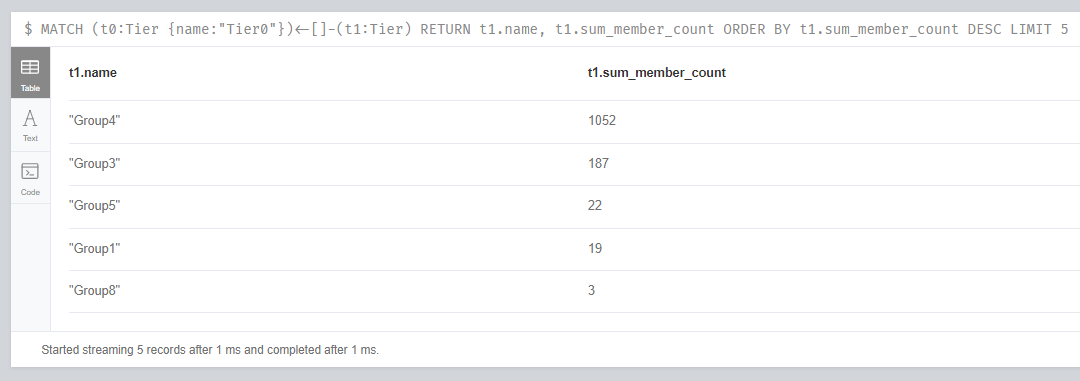
Risky groups and their sum_member_count values after analysis

